[Read More...]
Browse » Home » Archives for July 2011
What are Secure Sockets Layer (SSL)
12:10 AM
Devendra
Hey guyzz today i m providing you a brief information about SSL , as they are modern means of securing your data tranferring from server to USER hope u like it.
Secure Sockets Layer (SSL) is the most widely used technology for providing a secure communication between the web client and the web server. Most of us are familiar with many sites such as Gmail, Yahoo etc. using https protocol in their login pages. When we see this, we may wonder what’s the difference between http and https. In simple words HTTP protocol is used for standard communication between the Web server and the client. HTTPS is used for a SECURE communication.

What exactly is Secure Communication ?
Suppose there exists two communication parties A (client) and B (server).
Working of HTTP
When A sends a message to B, the message is sent as a plain text in an unencrypted manner. This is acceptable in normal situations where the messages exchanged are not confidential. But imagine a situation where A sends a PASSWORD to B. In this case, the password is also sent as a plain text. This has a serious security problem because, if an intruder (hacker) can gain unauthorised access to the ongoing communication between A and B , he can see the PASSWORDS since they remain unencrypted. This scenario is illustrated using the following figure
Now lets see the working of HTTPS
When A sends a PASSWORD (say “mypass“) to B, the message is sent in an encrypted format. The encrypted message is decrypted on B‘s side. So even if the Hacker gains an unauthorised access to the ongoing communication between A and B he gets only the encrypted password (“xz54p6kd“) and not the original password. This is shown below
How is HTTPS implemented ?
HTTPS is implemented using Secure Sockets Layer (SSL). A website can implementHTTPS by purchasing an SSL Certificate. Secure Sockets Layer (SSL) technology protects
a Web site and makes it easy for the Web site visitors to trust it. It has the following uses
1. An SSL Certificate enables encryption of sensitive information during online transactions.2. Each SSL Certificate contains unique, authenticated information about the certificate owner.3. A Certificate Authority verifies the identity of the certificate owner when it is issued.
How Encryption Works ?
Each SSL Certificate consists of a Public key and a Private key. The public key is used to encrypt the information and the private key is used to decrypt it. When your browser connects to a secure domain, the server sends a Public key to the browser to perform the encryption. The public key is made available to every one but the private key(used for decryption) is kept secret. So during a secure communication, the browser encrypts the message using the public key and sends it to the server. The message is decrypted on the server side using the Private key(Secret key).
How to identify a Secure Connection ?
In Internet Explorer, you will see a lock icon in the Security Status bar. The Security Status bar is located on the right side of the Address bar. You can click the lock to view the identity of the website.
in the Security Status bar. The Security Status bar is located on the right side of the Address bar. You can click the lock to view the identity of the website.
In high-security browsers, the authenticated organization name is prominently displayed and the address bar turns GREEN when an Extended Validation SSL Certificate is detected. If the information does not match or the certificate has expired, the browser displays an error message or warning and the status bar may turn RED.
So the bottom line is, whenever you perform an online transaction such as Credit card payment, Bank login or Email login always ensure that you have a secure communication. A secure communication
Due to SSl certificates the chances of phishing ,session hijacking attacks are reduced because phishing attack cant be carried on https.
Secure Sockets Layer (SSL) is the most widely used technology for providing a secure communication between the web client and the web server. Most of us are familiar with many sites such as Gmail, Yahoo etc. using https protocol in their login pages. When we see this, we may wonder what’s the difference between http and https. In simple words HTTP protocol is used for standard communication between the Web server and the client. HTTPS is used for a SECURE communication.
What exactly is Secure Communication ?
Suppose there exists two communication parties A (client) and B (server).
Working of HTTP
When A sends a message to B, the message is sent as a plain text in an unencrypted manner. This is acceptable in normal situations where the messages exchanged are not confidential. But imagine a situation where A sends a PASSWORD to B. In this case, the password is also sent as a plain text. This has a serious security problem because, if an intruder (hacker) can gain unauthorised access to the ongoing communication between A and B , he can see the PASSWORDS since they remain unencrypted. This scenario is illustrated using the following figure
Now lets see the working of HTTPS
When A sends a PASSWORD (say “mypass“) to B, the message is sent in an encrypted format. The encrypted message is decrypted on B‘s side. So even if the Hacker gains an unauthorised access to the ongoing communication between A and B he gets only the encrypted password (“xz54p6kd“) and not the original password. This is shown below
How is HTTPS implemented ?
HTTPS is implemented using Secure Sockets Layer (SSL). A website can implementHTTPS by purchasing an SSL Certificate. Secure Sockets Layer (SSL) technology protects
a Web site and makes it easy for the Web site visitors to trust it. It has the following uses
1. An SSL Certificate enables encryption of sensitive information during online transactions.2. Each SSL Certificate contains unique, authenticated information about the certificate owner.3. A Certificate Authority verifies the identity of the certificate owner when it is issued.
How Encryption Works ?
Each SSL Certificate consists of a Public key and a Private key. The public key is used to encrypt the information and the private key is used to decrypt it. When your browser connects to a secure domain, the server sends a Public key to the browser to perform the encryption. The public key is made available to every one but the private key(used for decryption) is kept secret. So during a secure communication, the browser encrypts the message using the public key and sends it to the server. The message is decrypted on the server side using the Private key(Secret key).
How to identify a Secure Connection ?
In Internet Explorer, you will see a lock icon
 in the Security Status bar. The Security Status bar is located on the right side of the Address bar. You can click the lock to view the identity of the website.
in the Security Status bar. The Security Status bar is located on the right side of the Address bar. You can click the lock to view the identity of the website.In high-security browsers, the authenticated organization name is prominently displayed and the address bar turns GREEN when an Extended Validation SSL Certificate is detected. If the information does not match or the certificate has expired, the browser displays an error message or warning and the status bar may turn RED.
So the bottom line is, whenever you perform an online transaction such as Credit card payment, Bank login or Email login always ensure that you have a secure communication. A secure communication
Due to SSl certificates the chances of phishing ,session hijacking attacks are reduced because phishing attack cant be carried on https.
How To Customize Google Plus profile | how to change theme of google +
4:08 AM
Devendra
Google+ Ultimate (Google Plus Ultimate) is the Google Plus extensioin for G Chrome, which will get you to customize and to add more great look to your classic G plus profile. You just need to download and install this great Google+ Chrome extension to Customize Google Plus Profile
Features of Google+ Ultimate extension :
Features of Google+ Ultimate extension :
- Create Streams and new left-sidebar
- Change the background of the G Plus Page
- Get notifications while viewing any website
- Get your Chat Bar moved any where
- Reduce the size of G+ images
- Gets your profile look very good
How to Convert A Word Document To Pdf Online for free
3:56 AM
Devendra
Word Document to PDF converters are maximum used as this is very useful in offices, banks, etc. Another great requirement for converting word to pdf file is its good and original layout.
Here I have provided a way to convert word document to Pdf online, just follow this easy steps :
Here I have provided a way to convert word document to Pdf online, just follow this easy steps :
- Just go to PDFonline and then click on Browse
- Now select your word file and then give the desired name
- Provide your correct email address and then click on "convert to pdf"
- You will riceve converted file in your in-box or spam folder within 5 min.
hope you like this post..:)
ClubHack Magazine July 2011 released |E-Book|
8:32 AM
Devendra
CLubHACk has released the July 2011 version of their Magazine.
Topics contains:
- Tech Gyan: Using Metasploit with Nessus Bridge on Ubuntu
- Legal Gyan: Trademark Law and Cyberspace
- Tool Gyan: Armitage - The Ultimate Attack Platform for Metasploit
- Matrix Vibhag: The Exploitation Ka Baap MSF
- Mom's Guide: Penetration Testing with Metasploit Framework
Download Clubhack Magazine Issue (July 2011) from here: Download
What should you do when your gmail/yahoo account gets hacked?
9:11 AM
Devendra
How to Recover Hacked Email Accounts?
For Gmail:
It can be a big disaster if your Gmail account has been compromised as it may be associated with several services like Blogger, Analytics, Adwords, Adsense, Orkut etc. Losing access to your Gmail account means losing access to all the services associated it with too. Here is a list of possible recovery actions that you can try.
Step -1: Try resetting your password since it is the easiest way to get your account back in action. In this process Google may ask you to answer the secret question or may send the password reset details to the secondary email address associated with your compromised account. You can reset you password from the following link
If you cannot find success from the Step-1 then proceed to Step-2.
Step-2: Many times the hacker will change the secret question and secondary email address right after the account is compromised. This is the reason for the Password Reset process to fail. If this is the case then you need to contact the Gmail support team by filling out the account recovery form. This form will ask you to fill out several questions like
1. Email addresses of up to five frequently emailed contacts
2. Names of any 4 Labels that you may have created in your account
3. List of other services associated with your compromised account
4. Your last successful login date
5. Account created date
6. Last password that you remember and many more…
2. Names of any 4 Labels that you may have created in your account
3. List of other services associated with your compromised account
4. Your last successful login date
5. Account created date
6. Last password that you remember and many more…
You need to fill out this form as much accurately as possible. It is obvious to forget the dates of last login, account creation and similar terms. However you need to figure out the closest possible date/answers and fill out this form. This is your last chance! The more accurate the information filled out in the recovery form, the more the chances of getting your account back. You may reach the account recovery page form the following link
For Yahoo and Hotmail:
Unfortunately for Yahoo/Hotmail there is no second option like filling out the form or contacting the support team. All you need to do is either answer the secret questions that you have setup or reset the password using the secondary email option.
To initiate the password reset process just click on the Forgot password link in your login page and proceed as per the screen instructions.
I hope this post will help you recover the lost account.
how to create a Raw file[mp3,doc,jpg..etc] of any size with command prompt
12:36 AM
Devendra
create file with any size
1. goto run >type CMD [run as administrator],
2. now after openin cmd prompt you have to type a simple command:
"fsutil file createnew [filename] [size]" without quotes
"fsutil file createnew [filename] [size]" without quotes
for example : i want create file .mp3 with size 1gb.
so command is
so command is
fsutil file createnew abc.mp3 1000000000
3.now press enter it will give u the location of file, which is c:\windows\system32.
3.now press enter it will give u the location of file, which is c:\windows\system32.
Download Avast Antivirus Full Version Free 2011
10:58 AM
Devendra
Download Avast Antivirus Full versionFor Free 2011 is in great demand as Avast Anti virus is the best known virus defender in the world, but all can't afford its high cost software. So I got new way to Download Avast Antivirus Fullversion free for one year. You just need to enter your email and the download link along with 1 year free licsense key for Avast Internet Security or Antivirus will be send to you.
Download Avast Antivirus Full Version Free 2011 - Features of Avast Antivirus
- Best and improved Antivirus and anti-spyware engine
- Real-time anti-rootkit and anti-spy protection
- Silent and best firewalls to stop Hackers and other unauthorized access
- Great Anti-Spam protection for unwanted advertisements, etc
- Online Website surfing security
- New Boot-Time Scanner
- Latest Safe Zone to recover your PC instantly during emergency
- More powerful and intelligent scanner
- All automatic protection and in real time
Download Avast Antivirus Full Version Free 2011 - Genuine 1 year license key
- Just visit Avast Official Free registration page
- You will get the Free and Genuine 1 year Avast License key in your email
- Now Download latest version of Avast Anti Virus from the official site
- Install it and use the provided free license key
How to do Desktop phishing | Tutorial on desktop phishing
9:35 AM
Devendra
hey guyzz first understand the concept behind desktop phishing:

Difference between phishing and desktop phishing is as follows.
In phishing
1. Attacker convinces the victim to click on the link of fake login page which resembles a genuine login page.
2.Victim enters his credentials in fake login page that goes to attacker.
3. Victim is then redirected to an error page or genuine website depending on attacker.
But main drawback in phishing is that victim can easily differentiate between fake and real login page by
looking at the domain name. We can overcome this in desktop phishing by spoofing domain name.
In desktop phishing
1. Attacker sends an executable file to victim and victim is supposed to double click on it. Attacker's job is done.
2. Victim types the domain name of orignal/genuine website and is taken to our fake login page.
But the domain name remains the same as typed by victim
and victim doesn't come to know.
3. Rest of the things are same as in normal phishing.
What is Hosts File ?
The hosts file is a text file containing domain names and IP address associated with them.
Location of hosts file in windows: C:\Windows\System32\drivers\etc\
Whenever we visit any website, say www.anything.com , an query is sent to Domain Name Server(DNS) to
look up for the IP address associated with that website/domain. But before doing this the hosts file on our local computer is checked for the IP address associated to the domain name.
Suppose we make an entry in hosts file as shown. When we visitwww.anywebsite.com , we would
be taken to this 115.125.124.50. No query for resolving IP address associated with www.anywebsite.com would be sent to DNS.
What is the attack ?
I hope you have got an idea that how modification of this hosts file on victim's computer can be misused.
We need to modify victim's hosts file by adding the genuine domain name and IP address of our
fake website /phishing page. Whenever victim would visit the genuine website , he would be directed to our fake login page
and domain name in the URL box would remain genuine as typed by victim. Hence domain name is spoofed.
follow these simple Steps to perform attack:
1. Host phishing page on your computer.
Since the webshosting sites like 110mb.com,ripway.com etc where we usually upload our phishing page do not provide a IP that points to your website likewww.anything.110mb.com. An IP address points to a webserver and not a website. So we need to host the phishing page on our computer using a webserver software like wamp or xampp.
Download the wamp or xampp.
2.Modify Hosts file.
If you dont have physical access to victim's computer. Then copy your hosts file and paste anywhere.
Edit it with any text editor and associate your public IP address with domain you wish as show.
Like in this case , when victim would visit gmail.com , he would be take to website hosted on IP 'xxx.xxx.xxx.xxx'.
Replace it with your public IP.
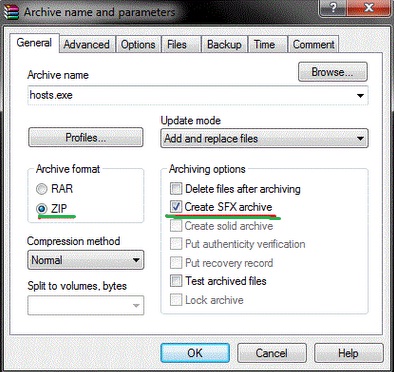
3. Compress hosts file such that when victim opens it, it automatically gets copied to default
location C:\Windows\system32\drivers\etc and victim's hosts file get replaced by our modified hosts file.
The you can bind this file with any exe using a binder or directly give it to victim. He is supposed to click it
and you are done .
NOTE:Limitations of attack :
1.Since our pubilc IP address is most probably dynamic that it gets changed everytime we disconnect and
connect. To overcome this we need to purchase static IP from our ISP.
2. The browser may warn the victim that Digital Certificate of the website is not genuine.

Difference between phishing and desktop phishing is as follows.
In phishing
1. Attacker convinces the victim to click on the link of fake login page which resembles a genuine login page.
2.Victim enters his credentials in fake login page that goes to attacker.
3. Victim is then redirected to an error page or genuine website depending on attacker.
But main drawback in phishing is that victim can easily differentiate between fake and real login page by
looking at the domain name. We can overcome this in desktop phishing by spoofing domain name.
In desktop phishing
1. Attacker sends an executable file to victim and victim is supposed to double click on it. Attacker's job is done.
2. Victim types the domain name of orignal/genuine website and is taken to our fake login page.
But the domain name remains the same as typed by victim
and victim doesn't come to know.
3. Rest of the things are same as in normal phishing.
What is Hosts File ?
The hosts file is a text file containing domain names and IP address associated with them.
Location of hosts file in windows: C:\Windows\System32\drivers\etc\
Whenever we visit any website, say www.anything.com , an query is sent to Domain Name Server(DNS) to
look up for the IP address associated with that website/domain. But before doing this the hosts file on our local computer is checked for the IP address associated to the domain name.
Suppose we make an entry in hosts file as shown. When we visitwww.anywebsite.com , we would
be taken to this 115.125.124.50. No query for resolving IP address associated with www.anywebsite.com would be sent to DNS.
What is the attack ?
I hope you have got an idea that how modification of this hosts file on victim's computer can be misused.
We need to modify victim's hosts file by adding the genuine domain name and IP address of our
fake website /phishing page. Whenever victim would visit the genuine website , he would be directed to our fake login page
and domain name in the URL box would remain genuine as typed by victim. Hence domain name is spoofed.
follow these simple Steps to perform attack:
1. Host phishing page on your computer.
Since the webshosting sites like 110mb.com,ripway.com etc where we usually upload our phishing page do not provide a IP that points to your website likewww.anything.110mb.com. An IP address points to a webserver and not a website. So we need to host the phishing page on our computer using a webserver software like wamp or xampp.
Download the wamp or xampp.
- Copy your phishing page and paste it in the WWW directory in wamp, the default path is "C:\Wamp\WWW"
- Run Wamp server on your pc
- Right click the wamp icon in the system tray and select Start all services, Visit your public IP address and you must see your phishing page
2.Modify Hosts file.
If you dont have physical access to victim's computer. Then copy your hosts file and paste anywhere.
Edit it with any text editor and associate your public IP address with domain you wish as show.
Like in this case , when victim would visit gmail.com , he would be take to website hosted on IP 'xxx.xxx.xxx.xxx'.
Replace it with your public IP.
3. Compress hosts file such that when victim opens it, it automatically gets copied to default
location C:\Windows\system32\drivers\etc and victim's hosts file get replaced by our modified hosts file.
The you can bind this file with any exe using a binder or directly give it to victim. He is supposed to click it
and you are done .
NOTE:Limitations of attack :
1.Since our pubilc IP address is most probably dynamic that it gets changed everytime we disconnect and
connect. To overcome this we need to purchase static IP from our ISP.
2. The browser may warn the victim that Digital Certificate of the website is not genuine.
Subscribe to:
Posts (Atom)
Latest From us
Instructions
THIS WEBSITE IS BUILT BY ME FOR EDUCATIONAL PURPOSE. IF YOU USE THIS INFORMATION TO HARM ANY SUBSTANCE OR COMMUNITY PERSONALLY AND GOT CAUGHT THAN WE ARE NOT RESPONSIBLE, EXPAND YOUR INFORMATION,SHARE UR THOUGHTS AND KNOWLEDGE WITH US. MAIL ME ON RRRICKY.SAINI2@GMAIL.COM












 Previous Article
Previous Article

